Ndubuisi Ekekwe
AUTHOR: Ndubuisi Ekekwe
Working or Living Abroad, Pillars to Build Thriving Business in Nigeria
You live in London or New York or anywhere for that matter. You have accumulated capabilities and want to start a business in Nigeria....
Agtech Opportunity to Relocate to Switzerland with CHF 30,000
Zenvus was invited to apply for this - apply to move to Switzerland. We do get a lot of it. Of course, no one...
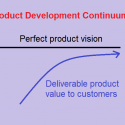
The Greatest Mistake – Attaining PERFECT Product Vision
The greatest phase to attend in any product vision is PERFECTION. Reaching that point is a huge mistake. Yes, any company that does that...
How Two Nigerian Companies are Growing with One Oasis Strategy
In organizations around the world, resources are scarce. Firms have to optimize the factors of production as they create products and services while pursuing...
The Brilliance of the New Konga Strategy
The Punch wrote a piece today where it quoted the CEO of Konga, Nick Imudia. The business leader revealed his strategy to redesign not just...