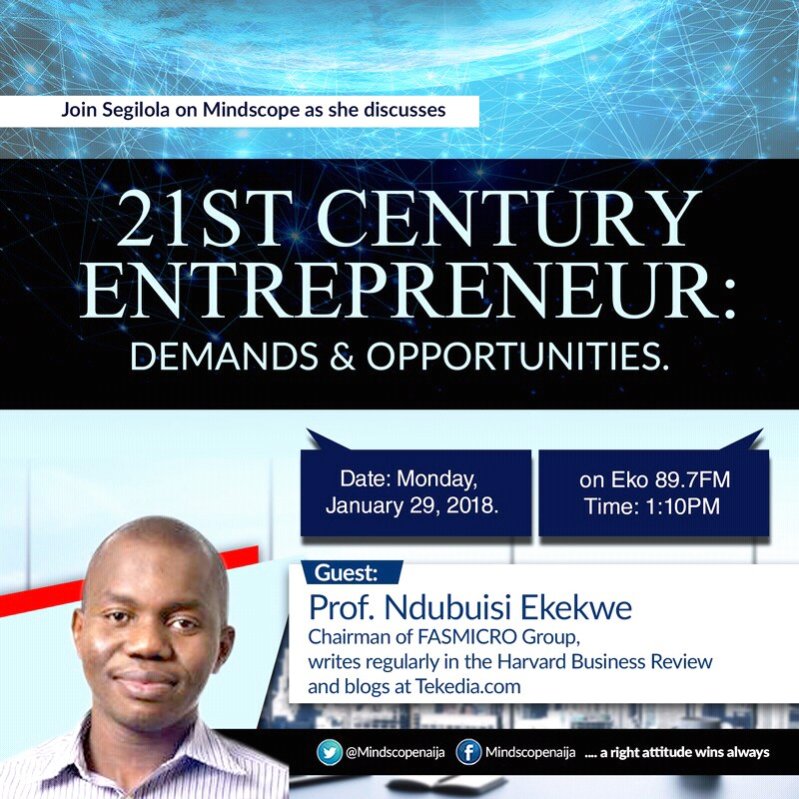
Good people, join me on Monday Jan 29th at Eko89.7fm. I would be discussing 21st Century Entrepreneur: Demands and Opportunities. Segilola would be the host.
Let us have a conversation on technology, business and innovation all within the constructs of Naija. It is about positioning for opportunities which are unbounded.