Ndubuisi Ekekwe
AUTHOR: Ndubuisi Ekekwe
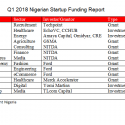
Nigerian Startups Raised $9.3 Million in Q1 2018
Techpoint has put together the Q1 2018 funding universe of Nigerian startups. The total is about $9.3 million. Q2 which covers April - June...
My Schedule in the European Commission, Brussels, Next Week
Beginning this weekend, I will be working in Brussels, spending time in the European Commission all through next week. During this period, I will...
State of the Tech Nation – an Address by Ndubuisi Ekekwe
We want to thank companies and entrepreneurs who have registered for my upcoming workshop in Lagos. Also, we have listened that you want a...
The Next Wave: Making Native Blockchain Websites and Apps
In the next five years, blockchain will have real plays in Nigerian businesses and building native blockchain applications would be huge opportunities. We would have...
The Most Important Factor when Raising Money for Startups
The MAIN factor that matters when raising money is building a good company. Other things like the slides, the suits, the no-suits, the pitch...