The world was cyber-saved from WannaCry by a 22-year old man. Yes, when computers across the world were hit by a major ransomware attack over the weekend, pandemonium ensued. WannaCry was targeting both end users as well as corporate servers, locking them down and extorting an unlock fee from the victims. The worst part was how the malware used a vulnerability in Windows to spread the infection among unpatched systems.
Despite Microsoft issuing an emergency patch for Windows XP, the action was too late to stem the tide of infections across the globe. Eventually, that first wave was broken apart by one single white hat hacker.
British cybersecurity researcher Marcus Hutchins, who goes by the name MalwareTech, was responsible for stopping the spread of the first wave of WannaCry’s infection. How? He just bought a website.
After WannaCry had gained its notoriety, the 22-year-old was studying the code responsible for the worldwide panic, in an effort to understand it. What he noticed was that, after infecting a system, WannCry contained a set of instructions directing it to check a gibberish URL. Curious to see why that was, Hutchins went ahead and registered the domain name mentioned in the code for around $10. And that little bit of curiosity bought security researchers valuable time, as it killed off the malware’s ability to infect other systems.
Experts believe the initial infections of WannaCry were carried out by phishing attacks through email, or by exploiting a network security hole. After that, the malware was capable of spreading itself using the exploit in Microsoft’s Windows vulnerability. However, it seems the malware’s creators had programmed a “kill switch” into it, in case they ever needed to quickly deactivate the infection. That’s why WannaCry kept checking the bogus URL each time it infected a new computer. The idea is that, as long as the URL wasn’t a live page, the infection would continue.
The minute Hutchins registered the domain, it stopped the malware’s ability to spread; a huge relief to security researchers, even if the infected systems still remained on lockdown. It gave people time to update and patch security vulnerabilities, especially in the US, where WannaCry was yet to effectively penetrate before the kill switch was found. Hutchins’ actions may have saved thousands of people from being the next line of victims by the malware.
Unfortunately, that next wave is already here. It didn’t take long after Hutchins’ discovery for newer versions of WannaCry to show up online, all lacking the safety kill switch their predecessor had. Of course, cybersecurity researchers are also hard at work, attempting to track down where WannaCry initiated from. Patching holes and updating security is well and good, but the only way to stop people from being victimised by malware they aren’t familiar with is to catch the perpetrators and stop the infection at the source.
Great For Cybersecurity Companies.
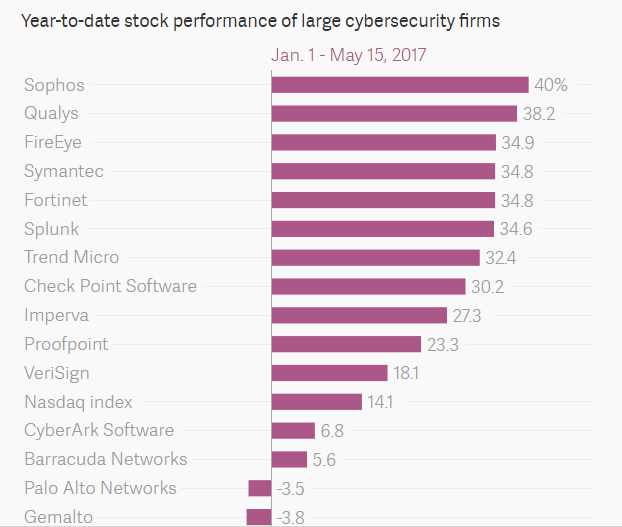
WannaCry has provided good advertising for cybersecurity companies around the world. The general constructs of cybersecurity in the last few weeks have been good for business. Symantec has jumped by around 4%, worth some $700 million in market cap. Companies like Fortinet, FireEye, Sophos, and Qualys have also jumped. F-Secure and Tokyo-listed Trend Micro also added a few percent to their share prices, worth several million dollars for each company. This is the state of the stock performances of major cybersecurity companies, according to Quartz. They are having one of the best years in a decade.
Like this:
Like Loading...