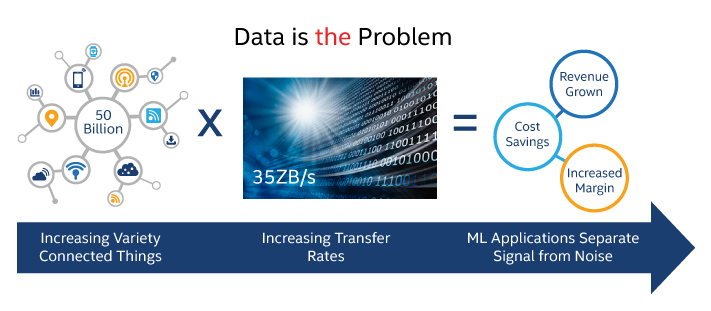
But first what is e-ticket?
You can read what is an electronic ticket for Adele concert and how to receive it with the help of our platform. The future of buying tickets is here!
Fast way to visit a concert
Electronic ticket it is a file (in pdf-format), which a client receives to his e-mail after making payment. To print such e-ticket, he may use any printer (colour or black and white). Each e-ticket has a special unique barcode, which distinguishes it from others. With the help of such barcode card is protected from unauthorised usage. Also, there should be written your name, title of the event and of course seat. To prevent unauthorised replicating of the ticket, it is not recommended to display its online photos and images. With the help of a website, the customer has a possibility to buy any electronic ticket for the desired event.
Listen to Adele
Everyone can get a seat to some special entertaining by visiting our website. It is easy to find what you want here. If for example, you decided to listen to famous singer then our platform can provide you such opportunity. For example, Adele concert tickets are now available.
This talented singer is known all over the world. Here are few facts about the history of the British vocalist Adele. Today she is known and adored in all continents; her voice can be heard on the radio. Her photos are on front pages of the leading tabloids. Adele was born in Tottenham, Great Britain. Being a child she has a strong voice and wide vocal range, she amazed everyone with her ability to sing beautifully and masterfully. She was admired by her friends, but still she did not believe in the success of her singing career. But Adele decided to show her vocal in the famous British School, where studied such celebrities as Amy Winehouse, Leona Lewis, and other British talents. It was successful, and best Britain teachers began to train her. The career of a singer started in 2006 when record company XL Recordings noticed her. Adele’s dreams became real. The first song, which is called «Hometown Glory» was released in October 2007. And the song was nominated for a Grammy Award. Also, song «Chasing Pavements», has reached the second line of the national charts in Britain.
Adele Adkins is one of the brightest musical events that appeared during the recent years. She has immensely strong, deep voice and natural charisma. Adele has done an impossible thing -she has shown that talent is an essential thing and it can overcome everything.
Adkins has broken all stereotypes. Success and glory of this smiling British woman seem incredible, but she deserves it.
So, to become a part of an amazing show of Adkins, find this artist by typing her name on the search panel. Don’t miss your unique chance to listen and enjoy this unordinary vocalist. Visit our reliable service right now. You can study more info about our company at the bottom of the page. There you will also see terms of use and our privacy policy. The funny crab will show you all available tickets and dates. Simply select ‘Buy Tickets’ green button then you will be redirected to checkout. The user must provide all necessary data, and then he will receive a seat in concert.