It has been a remarkably year, 2016, with its attendant successes and failures for people, industries and nations. More remarkably, it has been a year of great technological strides and achievements with innovations that provided avenues for solving big problems and opening up opportunities, ranging from self-driving cars to Advanced Robotics, Improved Data Science, Genomics, Improved Solar energy technologies etc.
Agricultural stakeholders and technology enthusiasts in Africa also witnessed the introduction of the Zenvus Technology, a unique innovation from a team of highly talented individuals led by Prof. Ndubuisi Ekekwe driven to exploit the ever burgeoning power of technology and science to revolutionize farming output efficiency and productivity in Africa.
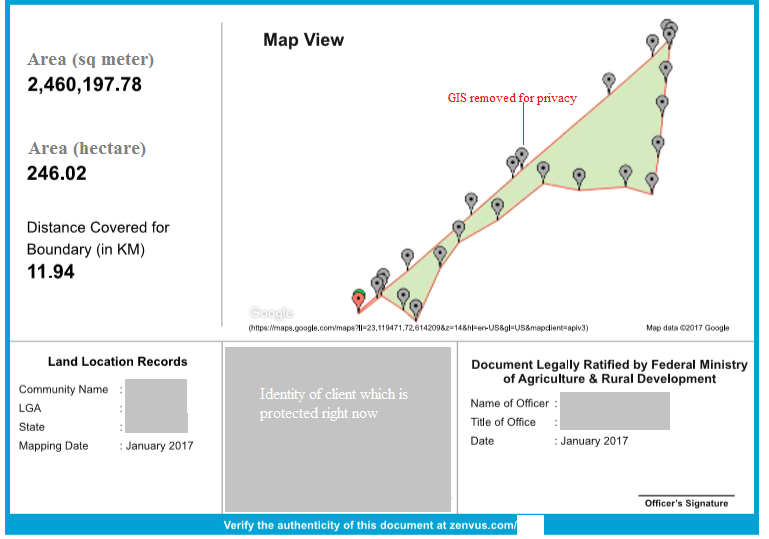
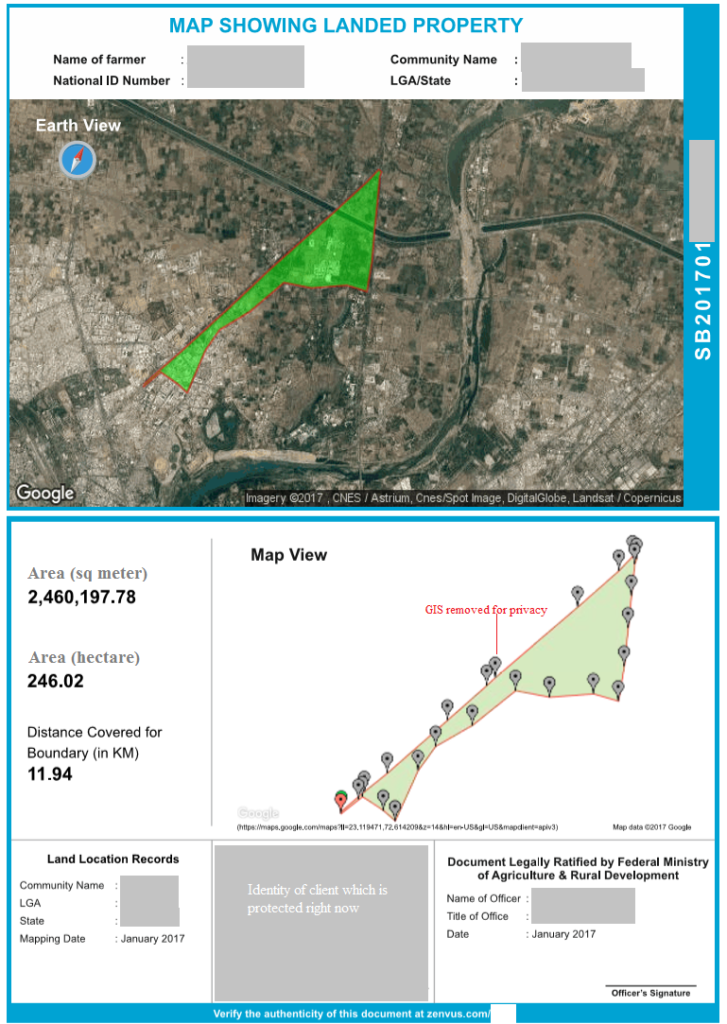
“Zenvus is an intelligent solution for farms that uses proprietary electronics sensors to collect soil data like moisture, nutrients, pH etc and send them to a cloud server via GSM, satellite or Wifi. Algorithms in the server analyze the data and advice farmers on farming. As the crops grow, the system deploys special cameras to build vegetative health to help detection of drought stress, pests and diseases. The data generated is aggregated, anonymized and made available via subscription for agro-lending, agro-insurance, commodity trading to banks, insurers and investors”. Prof Ndubuisi Ekekwe.
The Zenvus technology among other things would allow farmers and stakeholders make informed decisions by providing real time data for the farmers and stakeholders thus eliminating guesses on timing, procedure and crops for farming. Indeed, as the American Data Scientist W. Edward Feming quipped , “Without data, you are just another person with an opinion” we have long continued to rely on opinions and poor forecast to make decisions on Agricultural investments and this has taken a toll on agricultural yield. The technology also provides data analytics that relate information on possible outbreak of pests and diseases in farms which usually reduces yield, allowing farmers to initiate preventive measures.

This is a timely innovation for an industry that has been tipped to boost many economies in Africa with many African leaders pledging commitment towards Agriculture in the present and future. It is also a peerless stride in an industry seldom associated with innovation in Africa. However, as continuous push is being made for a deeper penetration of mechanized farming in Africa, it is necessary to remind ourselves that Agriculture has remained an industry driven by innovation and technology in the developed societies. Agricultural yields have been maximized through innovation, technology and science as demonstrated by countries like Israel. In the economic account of Israel in their phenomenal book, Start-up Nation, the authors recounted that President Shimon Peres had asserted that Agriculture is ninety-five percent science and five percent work. This drove his underlying commitment for innovation in Agriculture which saw Israel increase its agricultural yield seventeen times within twenty-five years.
The promise of this innovation is apparent and its impact is scalable and measurable. Little wonder that within months of its introduction, the technology was a finalist of the 2016 Singularity University Food Grand Challenge and have been featured in many leading technology reviews. The technology has also recorded noteworthy milestones within the last 6 months of launch, such as a grant support from Facebook to develop the artificial intelligence which will power farming decision making via Zenvus Bot which is on beta at the moment.
The technology has also been quickly adopted by leading Agricultural stakeholders and policy proponent in Africa. For instance, Zenvus will begin piloting its technology for African Development Bank which wants to deploy it across all farms it is providing funding. The Bank of Agriculture, Nigeria is also adopting Zenvus as the technology platform to drive agricultural innovation in Nigeria. More recently, Zenvus have signed a contract with an African farm union to support 12.2 million farmers from 2017.
Nonetheless, more commitment would be required by African governments and their respective social institutions towards delivering needed incentives that can encourage and support more farmers in integrating this technology to increase crop yield.
As Professor Joel Mokyr noted in his book, The Lever of Riches: Technological Creativity and Economic Progress.
…to encourage technological creativity and innovation in a society, …three conditions have to be satisfied,… there has to be a core group of ingenious and resourceful innovators who are both willing and able to challenge their physical environment for their improvement,… Secondly, economic and social institutions have to encourage these potential innovators by providing the right incentive structure and thirdly such society most encourage diversity and tolerance.
The team at Zenvus technology has done an exceptional job in developing this technology; it would be great if such technological creativity comes under the aegis of the governments and agricultural stakeholders in Africa who can devote resources towards scaling this technology for farmers because of the positive impact on farm productivity accruable to this technology. This could hold the key to more productive farming in Africa from 2017 going forward.
Image source: zenvus