The Nigerian insurance market is a paltry $1 billion (by premium sold) and that is for a country with more than 180 million people. (By comparison, the global market size is $4.55 trillion.) Over the years, Nigerian insurers have been unable to expand this market owing to lack of innovation.
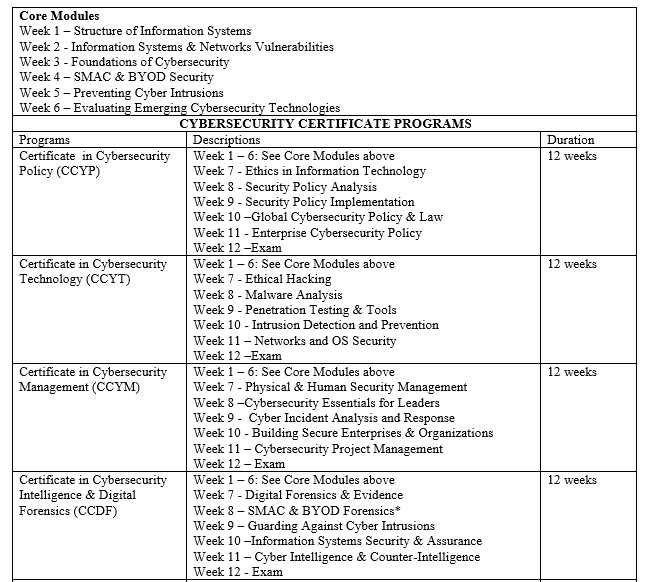
South Africa accounts for almost 80 per cent of all premiums in sub-Saharan Africa and the country has an insurance penetration rate — the total value of insurance premiums as a proportion of GDP — of about 13 per cent, well above the developed world average. Of the rest, Kenya is among the most advanced, with a penetration rate of 3 per cent. Nigeria’s, in comparison, is about 0.4 per cent, even though it is Africa’s most populous.
Indeed, except the websites these companies have, no technology innovation can be evident, on new products and services. They continue to sell stale and extremely lackluster products and services to Nigerian businesses and citizens.
They have missed opportunities which could have opened market growths for them. They are simply hoping that social attitude will change for Nigerians to begin to buy insurance, as they constantly blame the customers for their problems. Thinking outside the box with great products to change the mindsets of the consumes is not one of their strategies.
The Nigerian Insurance Industry
The Nigerian Insurance Industry includes the following sub-sectors: Composite, Non-life, Life and Reinsurance operators. Over the last five years, the Nigerian Insurance Industry has grown at a compound annual growth rate (CAGR) of 11%, buoyed by increased capitalization as well as the introduction of policies aimed at promoting the local market.
Nonetheless, the industry remains challenged with low apathy from the Nigerian populace and weak policy enforcement practices, resulting in a low penetration ratio of 0.4%. These challenges however present enormous opportunities when benchmarked with other African countries especially South Africa.
The Global Trajectory
Financial firms have long used rating agencies like Moody’s or S&P to judge the risk of bonds. Now, companies that face risk from cyber attacks—which these days is almost everyone—have a tool to do the same. African companies llost a total of $2 billion in 2016.
There is a trajectory to build a real business in this space. On Wednesday, CyberGRX unveiled a platform that acts as a clearinghouse for cyber risk. Developed by a group of blue chip security pros from companies like Blackstone and Aetna, CyberGRX promises to make the process of flagging cyber dangers from their vendors dramatically more efficient.
A Comprehensive Third Party Risk Management Platform Built by and with security practitioners, CyberGRX provides the most comprehensive third party cyber risk management platform, addressing the existing inefficiencies and creating benefit for both enterprises and for their partners and vendors. Through its innovative design, automation and advanced analytics, the CyberGRX platform enables enterprises to cost-effectively and collaboratively identify, assess, mitigate and monitor an enterprise’s cyber risk exposure across its entire vendor, partner and customer ecosystem.
The Nigerian Opportunity
Nigerian insurers through National Insurance Commission (NAICOM) and Nigerian Insurers Association (NIA) can come together to build a comprehensive tool like CyberGRX and use that to sell new type of policies in Nigeria. They can also use same to sell services to public companies through partnerships with Nigerian Stock Exchange. There will be opportunities in this space because cybersecurity risk is expanding in Nigeria. But to unlock the market, collaboration is key.
The opportunities will come via new business models underpinned by these business trends:
- Outsourcing
Organizations are relying on third-parties to improve the way systems function. And for good reason. Deloitte’s 2016 Global Outsourcing Survey found that businesses outsource to reduce costs and drive innovation. And all indicators suggest that outsourcing is here to stay.
- Yahoo boys are hungry
Last year, third party cyber attacks reached a tipping point. Businesses worldwide lost more than $400 billion to hackers. Nigeria is losing millions of dollars via cyber-attacks – $550 million in 2016.
- Regulatory requirements
Regulators, across all industries, are required to examine businesses on their compliance to cyber security laws. Some of the most common laws being, PCI, NERC, FISMA, HIPAA, SOX and GLBA. Recent trends in outsourcing and cybercrime have forced industry regulators to put pressure on organizations to better manage third party cyber risks.
Rounding Up
Digital ecosystems will continue to grow. Bad guys will continue to prey upon the path of least resistance – third parties. There will be opportunities for insurance firms to come together and build a new business model in the scope of CyberGRX in Nigeria. The product must help clients do the following:
- Plan: provide tiers tor third parties based on inherent risk factors.
- Assess: provides Risk Assessment as a Service (RAaaS) in the form of an on-site assessment or portal based self-assessment that is always up-to-date.
- Mitigate: prioritizes the most appropriate mitigation strategy and enables collaboration with your third party’s to reduce phone calls and emails.
- Monitor: continuous monitoring from the inside/out and outside/in. Correlate threat intelligence to weak controls to dynamically reprioritize levels of due diligence.
- Getting Assessed: offer simplified, straightforward, and comprehensive assessments.
Need Help?
These are many experts in this sector in Africa. One is Facyber which is a cybersecurity training and consulting firm. Another company is Kenya based Serianu.